Courtesy: http://searchengineland.com/how-to-increase-conversions-for-organic-keywords-75649
Once your website starts getting at least some traffic from organic search queries, you can help increase conversions (inquiries, signups, purchases, phone calls etc) by investigating what happens once people reach your website from the search results.
You can use Google Analytics to choose what keywords to focus on and to check the entrance pages (landing pages) for issues hurting conversions.
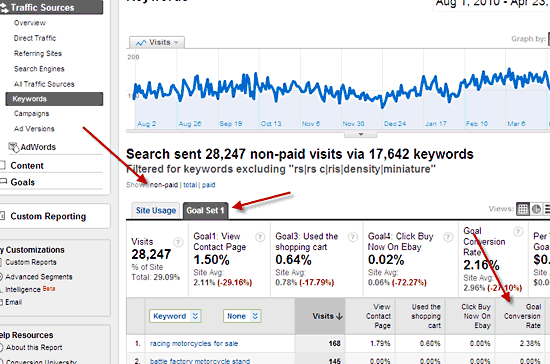
In Google Analytics, you should have either some important (non-ecommerce) conversion Goals being tracked or e-commerce turned on and set up so that it is tracking transactions. You’ll then be able to see the conversion rates by keyword as follows:
Scan through the list and more closely examine any keywords with a conversion rate that is lower than some minimal percentage.
You’ll likely notice a fair number of keywords with a conversion rate of zero. You’ll need to make a judgment call on each of these as to whether the phrase is relevant to the conversion goals of your site.
Sites tend to rank for many phrases that aren’t very relevant and are not likely to lead to conversions. Skip those and focus on the keyword phrases that you believe should be leading to conversions.

You’ll be presented with a list of the entrance pages for that keyword (You may have to click “non-paid” again on this page too).
Unfortunately, Google Analytics doesn’t turn the entrance page listings into links in this table, so you’ll either need to copy and append the URL segment in the listing to the website address in a browser address bar or follow the next steps.
Here’s what I do using two monitors. I open Analytics again in another instance of the browser on the other monitor and do the following:
When you click on the landing page you wish to examine a Content Detail page is presented. Click on the “visit this page” link you’ll see in the screen shot below to view the page.
Files with no navigation
We often see the content of frames (albeit less often these days) or orphaned “pages”, or the content from pop-up windows get indexed in search engines and viewed without any site navigation. In other words, people are clicking on the search results for these files and the page that they land on has no easy way for them to navigate into the rest of the web site.
For framed pages (if you still have this issue) determine if they really need to be developed as a frames system and rebuild them if not. There are also some JavaScript solutions to ensure that frames pages load correctly. Trying Binging “JavaScript ensure frames load correctly”.
Consider not using pop-up windows or putting the content of pop-up windows into a folder and disallow that folder in your robots.txt file. Recheck what entrance pages are being returned after a couple of months.
Old web pages still live
Webmasters often leave old web pages up on the site where they continue to get indexed by search engine. Many times I’ve seen entire old versions of websites moved to a folder on the site, but search engines find and index them. Sometimes, these old pages rank for important keywords.
Unfortunately, old web pages usually have broken navigation links and images, out of date information, and countless other issues. Consider setting up a 301 redirect from the old page(s) to the best page on the live site to capture that keyword traffic for awhile. Then work to optimize a page(s) on the live site for the keywords.
File not found
You may get “404 file not found” errors for many reasons. You’ll need to determine why this is happening for specific keyword phrases to decide if there are issues that need to be addressed. In some cases “file not found” errors are returned from search results because a web page was deleted or moved and the search engines haven’t removed the old URL from their listings yet.
Setup a 301 redirect for this URL to the best page on the live site. Recheck what entrance pages are being returned for the keywords wtihin a couple of weeks or months.
Here’s an example from a client’s site. They sell cooking products on their e-commerce website. They also publish their own book on a specific cooking topic which they sell on the site. People do search on the name of the book.
However, the top entrance page, the page ranking highest for the name of the book, was a page for a free recipe from the book. Not only was there no easy way to get to the page where one could by the book, nowhere on the page was it even mentioned that the book was for sale.
Once your website starts getting at least some traffic from organic search queries, you can help increase conversions (inquiries, signups, purchases, phone calls etc) by investigating what happens once people reach your website from the search results.
You can use Google Analytics to choose what keywords to focus on and to check the entrance pages (landing pages) for issues hurting conversions.
How To Choose Which Organic Keywords To Focus On
Most websites have hundreds or thousands of keywords bringing visitors to their website so it’s ideal to have an easy way to select which keywords to focus on.In Google Analytics, you should have either some important (non-ecommerce) conversion Goals being tracked or e-commerce turned on and set up so that it is tracking transactions. You’ll then be able to see the conversion rates by keyword as follows:
- Choose Traffic Sources / Keywords
- Set a date range of about 3 to 6 months (Less if you’ve made a fair number of changes to the site that might have affected rankings, changed URL’s etc)
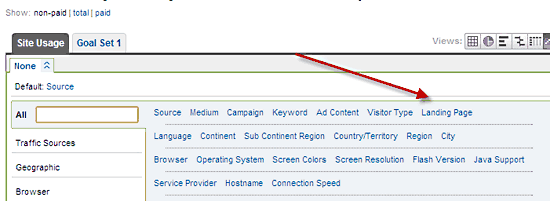
- Choose “Show: non-paid” (See the screen shot below)
- Then choose either a Goal Set tab or the Ecommerce tab (see the screen shot below)
Scan through the list and more closely examine any keywords with a conversion rate that is lower than some minimal percentage.
You’ll likely notice a fair number of keywords with a conversion rate of zero. You’ll need to make a judgment call on each of these as to whether the phrase is relevant to the conversion goals of your site.
Sites tend to rank for many phrases that aren’t very relevant and are not likely to lead to conversions. Skip those and focus on the keyword phrases that you believe should be leading to conversions.
Check The Entrance Pages For Issues
Although we have some control through optimization, it’s the search engines that decide what web pages rank high for organic keywords and thus become the entrance pages when people click through (unlike PPC where you choose the landing page) so the first step is to check any entrance page with more than a minimal number of entrances for issues.- In the Google Analytics table of keywords you generated, click on a keyword in the table that you want to examine.
- Next, click on the drop down selector you’ll see in the screen shot below

- Then select Landing Page (see in the screen shot below):

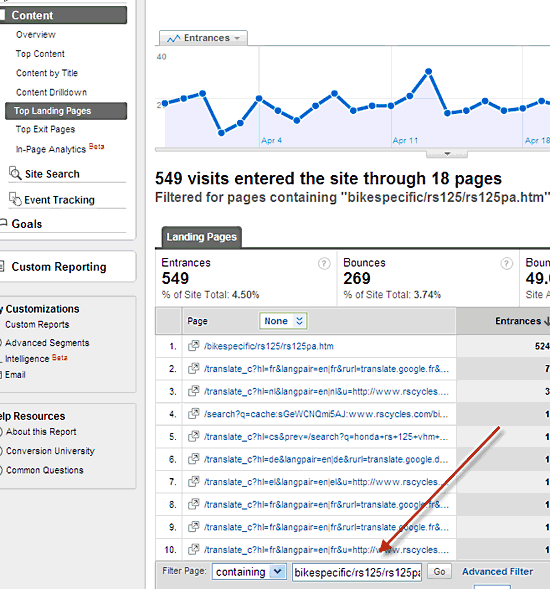
You’ll be presented with a list of the entrance pages for that keyword (You may have to click “non-paid” again on this page too).
Unfortunately, Google Analytics doesn’t turn the entrance page listings into links in this table, so you’ll either need to copy and append the URL segment in the listing to the website address in a browser address bar or follow the next steps.
Here’s what I do using two monitors. I open Analytics again in another instance of the browser on the other monitor and do the following:
- Choose Content / Top Landing Pages
- Select “containing” in the Filter option selector you’ll see in the screen shot below.
- Copy all or part of the URL segment from the keyword entrance page listing into the Filter field (see the screen shot below)
- This will generate a list of entrance pages that contain the URL segment.
- Click on the entrance page you want to examine.
When you click on the landing page you wish to examine a Content Detail page is presented. Click on the “visit this page” link you’ll see in the screen shot below to view the page.
Typical Issues With Organic Entrance Pages
Here are some typical issues we see with organic entrance pages along with some suggestions on how to handle them.Files with no navigation
We often see the content of frames (albeit less often these days) or orphaned “pages”, or the content from pop-up windows get indexed in search engines and viewed without any site navigation. In other words, people are clicking on the search results for these files and the page that they land on has no easy way for them to navigate into the rest of the web site.
For framed pages (if you still have this issue) determine if they really need to be developed as a frames system and rebuild them if not. There are also some JavaScript solutions to ensure that frames pages load correctly. Trying Binging “JavaScript ensure frames load correctly”.
Consider not using pop-up windows or putting the content of pop-up windows into a folder and disallow that folder in your robots.txt file. Recheck what entrance pages are being returned after a couple of months.
Old web pages still live
Webmasters often leave old web pages up on the site where they continue to get indexed by search engine. Many times I’ve seen entire old versions of websites moved to a folder on the site, but search engines find and index them. Sometimes, these old pages rank for important keywords.
Unfortunately, old web pages usually have broken navigation links and images, out of date information, and countless other issues. Consider setting up a 301 redirect from the old page(s) to the best page on the live site to capture that keyword traffic for awhile. Then work to optimize a page(s) on the live site for the keywords.
File not found
You may get “404 file not found” errors for many reasons. You’ll need to determine why this is happening for specific keyword phrases to decide if there are issues that need to be addressed. In some cases “file not found” errors are returned from search results because a web page was deleted or moved and the search engines haven’t removed the old URL from their listings yet.
Setup a 301 redirect for this URL to the best page on the live site. Recheck what entrance pages are being returned for the keywords wtihin a couple of weeks or months.
Is This The Best Entrance Page For The Keyword Phrase?
If there are no issues with an entrance page such as those pointed out in the previous section, consider whether it’s the best page for people to enter the site for this search query. The fact that you are examining the entrance page for this keyword phrase because the conversion rate is low would suggest that it may not be the best entrance page.Here’s an example from a client’s site. They sell cooking products on their e-commerce website. They also publish their own book on a specific cooking topic which they sell on the site. People do search on the name of the book.
However, the top entrance page, the page ranking highest for the name of the book, was a page for a free recipe from the book. Not only was there no easy way to get to the page where one could by the book, nowhere on the page was it even mentioned that the book was for sale.